Marcus Bebb-Jones: from poker fame to murder charge | ||||||
More than 12 years after the disappearance of his American wife, poker champion Marcus Bebb-Jones is a step closer to being extradited from the UK to face trial in the US for her murder.
The case has seen a number of bizarre twists that have yet to be explained.
These include Mr Bebb-Jones going on a Las Vegas "playboy weekend", partially funded by his wife's credit cards, then shooting himself in the head in a failed suicide attempt - all in the immediate aftermath of her disappearance.
In recent years he has had more attention for his successes on the online and casino poker circuit, winning thousands of pounds in prize money.
The large amount of cash he was thought to have accrued was one reason given for his being held in custody since his arrest. However, his barrister argued the money could not be used to aid his escape because it was "either spent or lost" and he was living on benefits.
Extradition to the US is a fate the Briton has been challenging since he was arrested at his home in Kidderminster, Worcestershire, last November.
Following a hearing in London on Monday district judge Howard Riddle will now send the case to the Home Secretary. If handed over and then convicted in the US, Mr Bebb-Jones would face a life sentence without the possibility of parole.
The judge rejected his lawyer's argument that such a sentence would be "grossly disproportionate" and would breach his human rights.
Mr Bebb-Jones's barrister Ben Cooper - who is also representing British computer hacker Gary McKinnon in his US extradition case - will now try to persuade the Secretary of State to let his client stay in the UK, and he will have the right to appeal against the eventual decision if necessary.
Right to remain silent
But if that process fails then, before long, Mr Bebb-Jones could be saying goodbye to his mother and 16-year-old son and boarding a flight with US marshals, who will travel to the UK to escort him back across the Atlantic.
He would then be collected by detectives and taken to the county jail in Glenwood Springs, Colorado - the state in which Mr Bebb-Jones' wife Sabrina's skull was found, on a mountain pass, nearly six years ago.
If and when he arrives there, he will find at least two people who are "looking forward" to seeing him.
Commander Bill Middleton and Detective Eric Ashworth, of Garfield County Sheriff's Office in Colorado, have been working on the case since that grisly find, and they are keen to see it brought to a conclusion.
"We have worked on this since September 2004, and the investigation has taken us to London, Dublin and Edinburgh to interview people.
"Now we are looking forward to sitting down and talking to him," Commander Middleton told BBC News.
However, Mr Bebb-Jones may decide to exercise his right to remain silent, he added.
Car cleaned
Mr Bebb-Jones had been living in Colorado with his wife, Sabrina, 31, and their son, Daniel, who was three when his mother vanished.
The couple owned the Hotel Melrose, in Grand Junction, and it was an employee who reported Sabrina missing on 18 September 1997, according to details of the court documents reported in local newspaper the Daily Sentinel.
Mr Bebb-Jones is said by prosecutors to have put forward a number of different stories as to what exactly happened and where, but in each he claimed his wife had walked out on him after an argument while they were out on a day trip.
More than one witness said the pair had gone on an outing to Dinosaur National Monument in north-west Colorado, and Mr Bebb-Jones is said to have told one friend of Sabrina's they had had a fight while there.
One employee said Mr Bebb-Jones had told her not to the call the police to report his wife missing, according to the report.
The employee also told police Mr Bebb-Jones had taken his minivan to the car wash to have the inside and outside cleaned, before taking his son to Las Vegas on 17 September. He told colleagues he was going to look for his wife, whose family live in the city.
According to US prosecutors, police later found Sabrina's blood inside the van.
Four days later Daniel was found alone in a Las Vegas hotel room and taken into state care. The next day a maid found Mr Bebb-Jones in another hotel room, with a "self-inflicted gunshot wound to the head".
Detectives said nearly $5,700 (£3,825) had been charged to credit cards - some of which were Sabrina's - in Las Vegas and a further $7,000 (£4,697) was refused. The spree is said to have included cash advances at casinos, hotel rooms and car rental.
No parole
Mr Bebb-Jones refused to talk to the US police, and moved back to the UK with his son in 1998, after selling the hotel.
For the next six years the case lay dormant, until a rancher found a human skull - later identified as Sabrina's - near Douglas Pass, which is between Dinosaur National Monument and Grand Junction.
The court document states that in the vicinity of the skull detectives found purple thistle flowers, which had also been discovered on the undercarriage of the couple's van in 1997.
Some 12 years after Sabrina's disappearance, a warrant was issued for Marcus Bebb-Jones in the US for murder in the first degree, concealing death and domestic violence.
Officers from the Metropolitan Police extradition unit acted on behalf of the US authorities, and Mr Bebb-Jones has been in custody awaiting the outcome of the extradition case.
On charges so serious, if found guilty the death penalty could be issued in the US.
But in accordance with the US-UK extradition treaty assurances have already been given that the sentence will not be used in this case.
However if Mr Bebb-Jones were to be found guilty following a trial he still faces staying in prison until his death.
As he awaits the final outcome of case from across the Atlantic, Commander Middleton says there is still much to explain.
| ||||||
Wednesday, May 8, 2013
Marcus Bebb-Jones: from poker fame to murder charge
Use a Software Bug to Win Video Poker? That’s a Federal Hacking Case
Use a Software Bug to Win Video Poker? That’s a Federal Hacking Case
- BY KEVIN POULSEN
- 05.01.13
- 6:00 AM

The Game King in an IGT promotional photo.
On Monday, July 6, 2009, two engineers from Nevada’s Gaming Control Board showed up at the Silverton Casino Lodge. The off-the-strip Soutfasseenth Las Vegas casino is best known for its mermaid aquarium, but the GCB geek squad wasn’t there to see swimmers in bikini tops and zip-on fish tails. They’d come to examine machine 50102, a Game King video poker unit on the casino floor that had been waiting for them, taped off like a crime scene, all weekend.
Manufactured by International Game Technology – a gambling leviathan that boasts $2 billion in revenue a year — the Game King is the ubiquitous workhorse of casino gambling, built to draw and keep gamblers who enjoy the fast pace and anonymity of machine play. Players can select from three cash levels and nearly three dozen different game variations, like Deuces Wild, Jacks or Better, Double Double Bonus and One-Eyes Jacks.
“All these guys did is simply push a sequence of buttons that they were legally entitled to push.”
A Vegas local named John Kane had been the final player at machine 50102, and he’d opted for Triple Play Triple Double Bonus Poker, winning three hands at once at the maximum $10 denomination. His last game was still on the screen: three aces, four aces, three aces again. At payout odds of 820-to-1 he’d scored an $8,200 bonanza.
But the casino had been suspicious, and Kane didn’t collect the last win. For one thing, Kane, now 54, had enjoyed a lot of big payouts that day: in about an hour he’d scored five jackpots large enough to require a hand pay and IRS paperwork. The GCB engineers yanked the machine’s logic tray and EEPROM and took them back to the lab.
There they discovered the secret behind Kane’s lucky streak: he was exploiting a previously-unknown firmware bug present in the Game King and nine other IGT machines – one that had been hidden for seven years.
Now Kane and the bug he exploited are at the center of a high-stakes legal battle before a federal judge in Las Vegas. The question: was it a criminal violation of federal anti-hacking law for Kane and a friend to knowingly take advantage of the glitch to the tune of at least half-a-million dollars? Prosecutors say it was. But in a win for the defense, a federal magistrate found last fall that the Computer Fraud and Abuse Act doesn’t apply, and recommended the hacking charge be dismissed. The issue is now being argued in front of U.S. District Court Judge Miranda Du, who’s likely to rule this month.
It’s the latest test of the Computer Fraud and Abuse Act, a 1986 law originally intended to punish hackers who remotely crack defense or banking computers over their 300 baud modems. Changes in technology and a string of amendments have pushed the law into a murky zone where prosecutors have charged people for violating website terms-of-service or an employer’s computer use policies. After the January suicide of Aaron Swartz, who’d been charged under the CFAA and other laws, Representative Zoe Lofgren (D-CA) drafted “Aaron’s Law” to reform the act. But that bill hasn’t been introduced. In the meantime, Andrew “Weev” Auernheimer was sentenced last March to three-and-a-half years in prison under the CFAA for running a script that downloaded 120,000 customer e-mail addresses that AT&T exposed on their iPad support website.
In the Game King case, the arguments are largely focused on whether Kane and his codefendant, Andre Nestor, exceeded their legal access to video poker machines by exploiting the bug. Kane’s attorney, Andrew Leavitt, says Kane played by the rules imposed by the machine, and that’s all that matters.
“What you see in most gambling cheating cases is the guy’s got a magnet in his boot or he’s shocking the machine with static electricity.” says Leavitt, a veteran Vegas defense attorney. “All these guys did is simply push a sequence of buttons that they were legally entitled to push.”
In court filings, prosecutors counter that the complex series of button-presses Kane and Nestor used to exploit the bug makes it more akin to computer hacking than poker-playing. As detailed in GCB’s report, attached to a defense filing (.pdf), the bug was indeed complex.
Kane began by selecting a game, like Triple Double Bonus Poker, and playing it at the lowest denomination the machine allows, like the $1.00 level. He kept playing, until he won a high payout, like the $820 at the Silverton.
Then he’d immediately switch to a different game variation, like straight “Draw Poker.” He’d play Draw Poker until he scored a win of any amount at all. The point of this play was to get the machine to offer a “double-up”, which lets the player put his winnings up to simple high-card-wins draw. Through whatever twist of code caused the bug, the appearance of the double-up invitation was critical. Machines that didn’t have the option enabled were immune.
“To allow customers to access previously played hands of cards, at will, would remove the element of chance and obviate the whole purpose of gambling. It would certainly be contrary to the rules of poker.”
At that point Kane would put more cash, or a voucher, into the machine, then exit the Draw Poker game and switch the denomination to the game maximum — $10 in the Silverton game.
Now when Kane returned to Triple Double Bonus Poker, he’d find his previous $820 win was still showing. He could press the cash-out button from this screen, and the machine would re-award the jackpot. Better yet, it would re-calculate the win at the new denomination level, giving him a hand-payout of $8,200.
It takes a lot of video poker play to stumble upon a bug like that. And Kane, according to his lawyer, played a lot of video poker. “He’s played more than anyone else in the United States,” claims Leavitt. “I’m not exaggerating or embellishing. … In one year he played 12 million dollars worth of video poker” and lost about a million, he says. “It’s an addiction.”
It was during one of his video poker binges that Kane discovered the bug. “He accidentally hit a button too soon, and presto,” says Leavitt, “It was a fluke. There was no research… Just playing.”
When Kane found the double-up bug in April 2009, he contacted Nestor in Pennsylvania. Nestor, now 41, flew out to Vegas, and over the following weeks one or both of the men allegedly showed up at the Fremont, the Golden Nugget, the Orleans, the Texas Station, Harrah’s, the Rio, the Wynn, and the Silverton, beating the house everywhere they went.
“These guys kind of kept it a secret,” says Leavitt. “If this had got out… this would have been a bad thing for the casinos.”
In June, Nestor returned to Pennsylvania, and began working the exploit with a crew. He showed up at the casino of the Meadows Racetrack in Washington County with ex-cop Kelly Laverde, who acted as Nestor’s bodyguard, occasionally flashing his old police badge to casino staff. Nestor’s associate Patrick Loushil tagged along to collect some of the payouts, perhaps so they didn’t all wind up on Nestor’s tax bill.
With all the appearance of a high-roller, complete with entourage, Nestor was able to persuade a casino staffer to enable the double-up feature on an IGT Draw Poker machine in the Meadows’ “high limit” room. A supervisor immediately reversed the decision, and the staffer went through the procedure to turn off the feature again, but neglected to save the change.
It would prove a costly mistake. Nestor and his crew returned to that same machine 15 times over the next two months, collecting $429,945 from 61 payouts. (Adding insult to injury, the Meadows was later fined $48,900 for turning on the double-up feature without regulator approval.)
As Nestor played in Pennsylvania, Kane continued to work Vegas, until the Silverton incident put the bug in front of the Gaming Control Board’s 25-person Technology Division. Formed in the mid-1980s as video gambling began its Las Vegas ascent, the Technology Division is the center of a vast software integrity operation: its computer and electrical engineers maintain a database of about 300,000 approved program variations, says its director. Over the course of three years, every location in Las Vegas with a gaming machine gets a visit from a GCB inspector, who cracks open the machines and checks the SHA-1 hashes against the database, to ensure that only approved code is taking money from the tourists.
The GCB also investigates suspected fraud and theft, sometimes reported by a casino, sometimes by a patron who’s convinced a game machine isn’t paying out properly. Much of the cheating the Technology Division deals with comes from professionals, who will buy a used game machine, put it in their garage and plumb it for vulnerabilities.
“They are looking to explore how they can exploit the machine from a mechanical standpoint,” says Jim Barbee, chief of the division. That means physical hacks aimed at the coin hopper or the bill reader. Software vulnerabilities like Kane’s are nearly unheard of. “I’ve been here about 14 years, and in my tenure, none pop into mind other than the one that you’re referring to,” he says. “Possibly one or two others, but it is an extreme rarity”’
Using the Silverton’s surveillance video as a tutorial, the GCB engineers quickly reproduced the Game King bug. They alerted IGT, which sent an urgent notice to its customers.
“Replacement programs are being expedited,” the company wrote on July 7, 2009. “It is important to note that some of these programs have been in the field over seven years without incident except for the recent issue.” Because the exploit would only work on units that had the double-up option available, IGT recommended that casinos disable that option as a work-around. (IGT declined to comment for this story).
Even after the notice, Nestor and his crew were still returning to the vulnerable Draw Poker machine at the Meadows, until August 28, 2009, when an agent of the Pennsylvania Gaming Control Board observed Nestor win a $20,000 jackpot and send his associate Loushil to collect it. An investigation followed, and the Pennsylvania GCB rediscovered the double-up bug themselves.
“Who would not win as much money as they could on a machine that says, ‘Jackpot’? That’s the whole idea!”
The local district attorney prosecuted Nestor on scores of charges. But on the first day of jury selection, U.S. marshals swooped in with an arrest warrant out of Las Vegas, where Nestor and Kane had been charged with federal wire fraud and computer hacking.
Interviewed by a local television crew on his way out of the Pennsylvania courthouse, Nestor was apoplectic.
“I’m being arrested federally for winning on a slot machine,” he said. “It’s just like if someone taught you how to count cards, which we all know is not illegal. You know. Someone told me that there are machines that had programming that gave a player an advantage over the house. And that’s all there is to it.…
“Who would not win as much money as they could on a machine that says, ‘Jackpot’? That’s the whole idea!”
Under the relevant section of the CFAA, Kane and Nestor aren’t charged with hacking into the Game King from the outside, but rather with exceeding their otherwise legitimate access “to obtain or alter information in the computer that the accesser is not entitled so to obtain or alter.”
“In short, the casinos authorized defendants to play video poker,” wrote Assistant U.S. Attorney Daniel Bogden. “What the casinos did not do was to authorize defendants ‘to obtain or alter information’ such as previously played hands of cards. To allow customers to access previously played hands of cards, at will, would remove the element of chance and obviate the whole purpose of gambling. It would certainly be contrary to the rules of poker.”
The “exceeds authorized access” provision of the CFAA is controversial. “Aaron’s Law” would strike that language entirely. But the bill hasn’t been introduced, and instead of reform, activists had to rally to tamp down yet another broadening of the CFAA last month – a draft bill that would have boosted sentences and made CFAA violations a RICO predicate. “In the middle of us pushing CFAA reform, this Bizarro proposal was floated by House Republicans making CFAA worse,” says EFF’s Trevor Timm.
The most serious rollback of the provision came, not from Congress, but from the U.S. 9th Circuit Court of Appeals in U.S. v Nosal, a case that stands now as Kane’s and Nestor’s best hope.
David Nosal was a former executive at a corporate recruiting firm who persuaded two employees to violate company policy and give him valuable information from the firm’s lead database. Prosecutors charged Nosal under the “exceeds authorized access” provision of the CFAA.
In April the 9th Circuit threw out those charges, noting that the firm employees didn’t hack into the database, they just violated company policy on what they’re allowed to do with the information within it. If that’s a crime under the CFAA, then so is violating the terms-of-service on a website, or watching sports highlights on ESPN.com on company time.
“For example, it’s not widely known that, up until very recently, Google forbade minors from using its services,” wrote chief judge Alex Kozinski. “Adopting the government’s interpretation would turn vast numbers of teens and pre-teens into juvenile delinquents.”
Nosal was later convicted at trial on other charges, but the appeals court ruling is a landmark, and it’s binding law in nine western U.S. states, including Nevada.
Last month Judge Du asked both sides in the Vegas case to weigh in on how the ruling changes things for them. “In light of United States v. Nosal … and the considerable legislative history demonstrating that Congress intended the CFAA to punish computer hacking, rather than computer misuse, was Defendants’ conduct comparable to hacking or misuse?” she asked in an April 15 order (.pdf).
“It’s a sign of progress, I think,” says Orin Kerr, a law professor at the George Washington University Law School, who’s representing, Andrew Auernheimer on appeal. “A few years ago, judges never questioned broad readings of the CFAA.”
Written filings are due on May 8, and the trial is currently set for August 20. If the CFAA charges are thrown out, Kane and Nestor still face wire fraud charges for their lucky streak. Leavitt, who spoke with Wired prior to the April 15 order, said he likes his odds on those counts. “They’re going to have real tough time with the wire fraud,” he says. “I never really understood why the federal government took this case in the first place.”
(Disclosure: As a hacker 20 years ago, the author pleaded guilty under an uncontroversial application of the CFAA.)
Are all telephone calls recorded and accessible to the US government?
A former FBI counterterrorism agent claims on CNN that this is the case
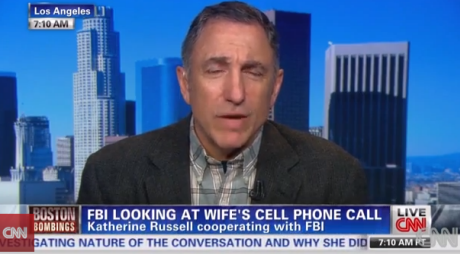
Former FBI counterterrorism agent Tim Clemente, on CNN, discussing government's surveillance capabilities Photograph: CNN screegrab
The real capabilities and behavior of the US surveillance state are almost entirely unknown to the American public because, like most things of significance done by the US government, it operates behind an impenetrable wall of secrecy. But a seemingly spontaneous admission this week by a former FBI counterterrorism agent provides a rather startling acknowledgment of just how vast and invasive these surveillance activities are.
Over the past couple days, cable news tabloid shows such as CNN's Out Front with Erin Burnett have been excitingly focused on the possible involvement in the Boston Marathon attack of Katherine Russell, the 24-year-old American widow of the deceased suspect, Tamerlan Tsarnaev. As part of their relentless stream of leaks uncritically disseminated by our Adversarial Press Corps, anonymous government officials are claimingthat they are now focused on telephone calls between Russell and Tsarnaev that took place both before and after the attack to determine if she had prior knowledge of the plot or participated in any way.
On Wednesday night, Burnett interviewed Tim Clemente, a former FBI counterterrorism agent, about whether the FBI would be able to discover the contents of past telephone conversations between the two. He quite clearly insisted that they could:
BURNETT: Tim, is there any way, obviously, there is a voice mail they can try to get the phone companies to give that up at this point. It's not a voice mail. It's just a conversation. There's no way they actually can find out what happened, right, unless she tells them?CLEMENTE: "No, there is a way. We certainly have ways in national security investigations to find out exactly what was said in that conversation. It's not necessarily something that the FBI is going to want to present in court, but it may help lead the investigation and/or lead to questioning of her. We certainly can find that out.BURNETT: "So they can actually get that? People are saying, look, that is incredible.CLEMENTE: "No, welcome to America. All of that stuff is being captured as we speak whether we know it or like it or not."
"All of that stuff" - meaning every telephone conversation Americans have with one another on US soil, with or without a search warrant - "is being captured as we speak".
On Thursday night, Clemente again appeared on CNN, this time with host Carol Costello, and she asked him about those remarks. He reiterated what he said the night before but added expressly that "all digital communications in the past" are recorded and stored:
Let's repeat that last part: "no digital communication is secure", by which he means not that any communication is susceptible to government interception as it happens (although that is true), but far beyond that: all digital communications - meaning telephone calls, emails, online chats and the like - are automatically recorded and stored and accessible to the government after the fact. To describe that is to define what a ubiquitous, limitless Surveillance State is.
There have been some previous indications that this is true. FormerAT&T engineer Mark Klein revealed that AT&T and other telecoms had built a special network that allowed the National Security Agency full and unfettered access to data about the telephone calls and the content of email communications for all of their customers. Specifically, Klein explained "that the NSA set up a system that vacuumed up Internet and phone-call data from ordinary Americans with the cooperation of AT&T" and that "contrary to the government's depiction of its surveillance program as aimed at overseas terrorists . . . much of the data sent through AT&T to the NSA was purely domestic." But his amazing revelations were mostly ignored and, when Congress retroactively immunized the nation's telecom giants for their participation in the illegal Bush spying programs, Klein's claims (by design) were prevented from being adjudicated in court.
That every single telephone call is recorded and stored would also explain this extraordinary revelation by the Washington Post in 2010:
Every day, collection systems at the National Security Agency intercept and store 1.7 billion e-mails, phone calls and other types of communications.
It would also help explain the revelations of former NSA official William Binney, who resigned from the agency in protest over its systemic spying on the domestic communications of US citizens, that the US government has "assembled on the order of 20 trillion transactions about US citizens with other US citizens" (which counts only communications transactions and not financial and other transactions), and that "the data that's being assembled is about everybody. And from that data, then they can target anyone they want."
Despite the extreme secrecy behind which these surveillance programs operate, there have been periodic reports of serious abuse. Two Democratic Senators, Ron Wyden and Mark Udall, have been warning for years that Americans would be "stunned" to learn what the US government is doing in terms of secret surveillance.

Strangely, back in 2002 - when hysteria over the 9/11 attacks (and thus acquiescence to government power) was at its peak - the Pentagon's attempt to implement what it called the "Total Information Awareness" program (TIA)sparked so much public controversy that it had to be official scrapped. But it has been incrementally re-instituted - without the creepy (though honest) name and all-seeing-eye logo - with little controversy or even notice.
Back in 2010, worldwide controversy erupted when the governments of Saudi Arabia and the United Arab Emirates banned the use of Blackberries because some communications were inaccessible to government intelligence agencies, and that could not be tolerated. The Obama administration condemned this move on the ground that it threatened core freedoms, only to turn around six weeks later anddemand that all forms of digital communications allow the US government backdoor access to intercept them. Put another way, the US government embraced exactly the same rationale invoked by the UAE and Saudi agencies: that no communications can be off limits. Indeed, the UAE, when responding to condemnations from the Obama administration, noted that it was simply doing exactly that which the US government does:
"'In fact, the UAE is exercising its sovereign right and is asking for exactly the same regulatory compliance - and with the same principles of judicial and regulatory oversight - that Blackberry grants the US and other governments and nothing more,' [UAE Ambassador to the US Yousef Al] Otaiba said. 'Importantly, the UAE requires the same compliance as the US for the very same reasons: to protect national security and to assist in law enforcement.'"
That no human communications can be allowed to take place without the scrutinizing eye of the US government is indeed the animating principle of the US Surveillance State. Still, this revelation, made in passing on CNN, that every single telephone call made by and among Americans is recorded and stored is something which most people undoubtedly do not know, even if the small group of people who focus on surveillance issues believed it to be true (clearly, both Burnett and Costello were shocked to hear this).
Some new polling suggests that Americans, even after the Boston attack, are growing increasingly concerned about erosions of civil liberties in the name of Terrorism. Even those people who claim it does not matter instinctively understand the value of personal privacy: they put locks on their bedroom doors and vigilantly safeguard their email passwords. That's why the US government so desperately maintains a wall of secrecy around their surveillance capabilities: because they fear that people will find their behavior unacceptably intrusive and threatening, as they did even back in 2002 when John Poindexter's TIA was unveiled.
Mass surveillance is the hallmark of a tyrannical political culture. But whatever one's views on that, the more that is known about what the US government and its surveillance agencies are doing, the better. This admission by this former FBI agent on CNN gives a very good sense for just how limitless these activities are.
Psychiatry’s Guide Is Out of Touch With Science, Experts Say
May 6, 2013
Psychiatry’s Guide Is Out of Touch With Science, Experts Say
By PAM BELLUCK and BENEDICT CAREY
Just weeks before the long-awaited publication of a new edition of the so-called bible of mental disorders, the federal government’s most prominent psychiatric expert has said the book suffers from a scientific “lack of validity.”
The expert, Dr. Thomas R. Insel, director of the National Institute of Mental Health, said in an interview Monday that his goal was to reshape the direction of psychiatric research to focus on biology, genetics and neuroscience so that scientists can define disorders by their causes, rather than their symptoms.
While the Diagnostic and Statistical Manual of Mental Disorders, or D.S.M., is the best tool now available for clinicians treating patients and should not be tossed out, he said, it does not reflect the complexity of many disorders, and its way of categorizing mental illnesses should not guide research.
“As long as the research community takes the D.S.M. to be a bible, we’ll never make progress,” Dr. Insel said, adding, “People think that everything has to match D.S.M. criteria, but you know what? Biology never read that book.”
The revision, known as the D.S.M.-5, is the first major reissue since 1994. It has stirred unprecedented questioning from the public, patient groups and, most fundamentally, senior figures in psychiatry who have challenged not only decisions about specific diagnoses but the scientific basis of the entire enterprise. Basic research into the biology of mental disorders and treatment has stalled, they say, confounded by the labyrinth of the brain.
Decades of spending on neuroscience have taught scientists mostly what they do not know, undermining some of their most elemental assumptions. Genetic glitches that appear to increase the risk of schizophrenia in one person may predispose others to autism-like symptoms, or bipolar disorder. The mechanisms of the field’s most commonly used drugs — antidepressants like Prozac, and antipsychosis medications like Zyprexa — have revealed nothing about the causes of those disorders. And major drugmakers have scaled back psychiatric drug development, having virtually no new biological “targets” to shoot for.
Dr. Insel is one of a growing number of scientists who think that the field needs an entirely new paradigm for understanding mental disorders, though neither he nor anyone else knows exactly what it will look like.
Even the chairman of the task force making revisions to the D.S.M., Dr. David J. Kupfer, a professor of psychiatry at the University of Pittsburgh, said the new manual was faced with doing the best it could with the scientific evidence available.
“The problem that we’ve had in dealing with the data that we’ve had over the five to 10 years since we began the revision process of D.S.M.-5 is a failure of our neuroscience and biology to give us the level of diagnostic criteria, a level of sensitivity and specificity that we would be able to introduce into the diagnostic manual,” Dr. Kupfer said.
The creators of the D.S.M. in the 1960s and ’70s “were real heroes at the time,” said Dr. Steven E. Hyman, a psychiatrist and neuroscientist at the Broad Institute and a former director at the National Institute of Mental Health. “They chose a model in which all psychiatric illnesses were represented as categories discontinuous with ‘normal.’ But this is totally wrong in a way they couldn’t have imagined. So in fact what they produced was an absolute scientific nightmare. Many people who get one diagnosis get five diagnoses, but they don’t have five diseases — they have one underlying condition.”
Dr. Hyman, Dr. Insel and other experts said they hoped that the science of psychiatry would follow the direction of cancer research, which is moving from classifying tumors by where they occur in the body to characterizing them by their genetic and molecular signatures.
About two years ago, to spur a move in that direction, Dr. Insel started a federal project called Research Domain Criteria, or RDoC, which he highlighted in a blog post last week. Dr. Insel said in the blog that the National Institute of Mental Health would be “reorienting its research away from D.S.M. categories” because “patients with mental disorders deserve better.” His commentary has created ripples throughout themental health community.
Dr. Insel said in the interview that his motivation was not to disparage the D.S.M. as a clinical tool, but to encourage researchers and especially outside reviewers who screen proposals for financing from his agency to disregard its categories and investigate the biological underpinnings of disorders instead. He said he had heard from scientists whose proposals to study processes common to depression, schizophrenia and psychosis were rejected by grant reviewers because they cut across D.S.M. disease categories.
“They didn’t get it,” Dr. Insel said of the reviewers. “What we’re trying to do with RDoC is say actually this is a fresh way to think about it.” He added that he hoped researchers would also participate in projects funded through the Obama administration’s new brain initiative.
Dr. Michael First, a psychiatry professor at Columbia who edited the last edition of the manual, said, “RDoC is clearly the way of the future,” although it would take years to get results that could apply to patients. In the meantime, he said, “RDoC can’t do what the D.S.M. does. The D.S.M. is what clinicians use. Patients will always come into offices with symptoms.”
For at least a decade, Dr. First and others said, patients will continue to be diagnosed with D.S.M. categories as a guide, and insurance companies will reimburse with such diagnoses in mind.
Dr. Jeffrey Lieberman, the chairman of the psychiatry department at Columbia and president-elect of the American Psychiatric Association, which publishes the D.S.M., said that the new edition’s refinements were “based on research in the last 20 years that will improve the utility of this guide for practitioners, and improve, however incrementally, the care patients receive.”
He added: “The last thing we want to do is be defensive or apologetic about the state of our field. But at the same time, we’re not satisfied with it either. There’s nothing we’d like better than to have more scientific progress.”
U.S. Weighs Wide Overhaul of Wiretap Laws
May 7, 2013
U.S. Weighs Wide Overhaul of Wiretap Laws
By CHARLIE SAVAGE
WASHINGTON — The Obama administration, resolving years of internal debate, is on the verge of backing a Federal Bureau of Investigation plan for a sweeping overhaul of surveillance laws that would make it easier to wiretap people who communicate using the Internet rather than by traditional phone services, according to officials familiar with the deliberations.
The F.B.I. director, Robert S. Mueller III, has argued that the bureau’s ability to carry out court-approved eavesdropping on suspects is “going dark” as communications technology evolves, and since 2010 has pushed for a legal mandate requiring companies like Facebook and Google to build into their instant-messaging and other such systems a capacity to comply with wiretap orders. That proposal, however, bogged down amid concerns by other agencies, like the Commerce Department, about quashing Silicon Valley innovation.
While the F.B.I.’s original proposal would have required Internet communications services to each build in a wiretapping capacity, the revised one, which must now be reviewed by the White House, focuses on fining companies that do not comply with wiretap orders. The difference, officials say, means that start-ups with a small number of users would have fewer worries about wiretapping issues unless the companies became popular enough to come to the Justice Department’s attention.
Still, the plan is likely to set off a debate over the future of the Internet if the White House submits it to Congress, according to lawyers for technology companies and advocates of Internet privacy and freedom.
“I think the F.B.I.’s proposal would render Internet communications less secure and more vulnerable to hackers and identity thieves,” said Gregory T. Nojeim of the Center for Democracy and Technology. “It would also mean that innovators who want to avoid new and expensive mandates will take their innovations abroad and develop them there, where there aren’t the same mandates.”
Andrew Weissmann, the general counsel of the F.B.I., said in a statement that the proposal was aimed only at preserving law enforcement officials’ longstanding ability to investigate suspected criminals, spies and terrorists subject to a court’s permission.
“This doesn’t create any new legal surveillance authority,” he said. “This always requires a court order. None of the ‘going dark’ solutions would do anything except update the law given means of modern communications.”
A central element of the F.B.I.’s 2010 proposal was to expand the Communications Assistance for Law Enforcement Act — a 1994 law that already requires phone and network carriers to build interception capabilities into their systems — so that it would also cover Internet-based services that allow people to converse. But the bureau has now largely moved away from that one-size-fits-all mandate.
Instead, the new proposal focuses on strengthening wiretap orders issued by judges. Currently, such orders instruct recipients to provide technical assistance to law enforcement agencies, leaving wiggle room for companies to say they tried but could not make the technology work. Under the new proposal, providers could be ordered to comply, and judges could impose fines if they did not. The shift in thinking toward the judicial fines was first reported by The Washington Post, and additional details were described to The New York Times by several officials who spoke on the condition of anonymity.
Under the proposal, officials said, for a company to be eligible for the strictest deadlines and fines — starting at $25,000 a day — it must first have been put on notice that it needed surveillance capabilities, triggering a 30-day period to consult with the government on any technical problems.
Such notice could be the receipt of its first wiretap order or a warning from the attorney general that it might receive a surveillance request in the future, officials said, arguing that most small start-ups would never receive either.
Michael Sussmann, a former Justice Department lawyer who advises communications providers, said that aspect of the plan appeared to be modeled on a British law, the Regulation of Investigatory Powers Act of 2000.
Foreign-based communications services that do business in the United States would be subject to the same procedures, and would be required to have a point of contact on domestic soil who could be served with a wiretap order, officials said.
Albert Gidari Jr., who represents technology companies on law enforcement matters, criticized that proposed procedure. He argued that if the United States started imposing fines on foreign Internet firms, it would encourage other countries, some of which may be looking for political dissidents, to penalize American companies if they refused to turn over users’ information.
“We’ll look a lot more like China than America after this,” Mr. Gidari said.
The expanded fines would also apply to phone and network carriers, like Verizon and AT&T, which are separately subject to the 1994 wiretapping capacity law. The FBI has argued that such companies sometimes roll out system upgrades without making sure that their wiretap capabilities will keep working.
The 1994 law would be expanded to cover peer-to-peer voice-over-Internet protocol, or VoIP — calls between computers that do not connect to the regular phone network. Such services typically do not route data packets through any central hub, making them difficult to intercept.
The F.B.I. has abandoned a component of its original proposal that would have required companies that facilitate the encryption of users’ messages to always have a key to unscramble them if presented with a court order. Critics had charged that such a law would create back doors for hackers. The current proposal would allow services that fully encrypt messages between users to keep operating, officials said.
In November 2010, Mr. Mueller toured Silicon Valley and briefed executives on the proposal as it then existed, urging them not to lobby against it, but the firms have adopted a cautious stance. In February 2011, the F.B.I.’s top lawyer at the time testified about the “going dark” problem at a House hearing, emphasizing that there was no administration proposal yet. Still, several top lawmakers at the hearing expressed skepticism, raising fears about innovation and security.
This article has been revised to reflect the following correction:
Correction: May 8, 2013
An earlier version of this article misspelled the surname of a former Justice Department lawyer who advises communications providers and commented on one aspect of the F.B.I.’s plan to overhaul surveillance laws. He is Michael Sussmann, not Sussman.
FBI claims right to read your e-mail, just like other federal agencies
FBI claims right to read your e-mail, just like other federal agencies
ECPA rears its ugly head again—despite DOJ's willingness to reform disliked law.
by Cyrus Farivar - May 8 2013, 2:30pm EDT
If we’ve told you once, we’ve told you a thousand times—the feds can (and do) easily access your e-mail. In fact, sending materials through the United States Postal Service is legally more secure than e-mail.
On Wednesday, as the result of a Freedom of Information Act request, the American Civil Liberties Union has published the first public copy of the 2012 edition of the FBI’s Domestic Investigations and Operations Guide. And this document clearly draws that distinction. The new disclosure shows that the FBI believes it does have the authority to open your e-mail essentially whenever it wants:
18.7.1.3.4.3 (U) MAIL OPENINGS(U) Mail in United States postal channels may be searched only pursuant to court order, or presidential authorization. United States Postal Service regulations governing such activities must be followed. A search of items that are being handled by individual couriers, or commercial courier companies, under circumstances in which there is a reasonable expectation of privacy, or have been sealed for deposit into postal channels, and that are discovered within properties or premises being searched, must be carried out according to unconsented FISA or FRCP Rule 41 physical search procedures.18.7.1.3.4.4 (U) COMPELLED DISCLOSURE OF THE CONTENTS OF STORED WIRE OR ELECTRONIC COMMUNICATIONS(U) Contents in "electronic storage" (e.g., unopened e-mail and voice mail) require a search warrant. See 18 U.S.c. § 2703(a). A distinction is made between the contents of communications that are in electronic storage (e.g., unopened e-mail) for less than 180 days and those in "electronic storage" for longer than 180 days, or those that are no longer in "electronic storage" (e.g., opened e-mail). In enacting the ECPA, Congress concluded that customers may not retain a "reasonable expectation of privacy" in information sent to network providers. However, the contents of an e-mail message that is unopened should nonetheless be protected by Fourth Amendment standards, similar to the contents of a regularly mailed letter. On the other hand, if the contents of an unopened message are kept beyond six months or stored on behalf oft he customer after the e-mail has been received or opened, it should he treated the same as a business record in the hands of a third party, such as an accountant or attorney. In that case, the government may subpoena the records from the third party without running afoul of either the Fourth or Fifth Amendment. If a search warrant is used, it may be served on the provider without notice to the customer or subscriber.
Here’s what all that means: under the much-maligned (but frustratingly still-current) 1986-era Electronic Communications Privacy Act (ECPA), law enforcement must get a warrant to access e-mail before it has been opened by the recipient. However, there are no such provisions once the e-mail has been opened or if it has been sitting in an inbox, unopened, for 180 days. In March 2013, the Department of Justice acknowledged in a Congressional hearing that this distinction no longer makes sense and the DOJ would support revisions to ECPA.
If that weren’t complicated enough, one United States circuit court of appeals decided that federal authorities do need a warrant before accessing e-mail. The case, known as United States v. Warshak, has created a split as other circuits haven’t yet taken up the issue, including the United States Supreme Court. (Google has since taken the public stance that it will follow the Warshakstandard.)
The ACLU has been at the forefront of trying to figure out exactly where various federal agencies stand in observing or not observing the Warshak standard. Just last month, the advocacy group unveiled the fact that the Internal Revenue Service believes it has the authority to investigate tax cheats under ECPA, but soon after the interim director said the agency has never done so.
Subscribe to:
Posts (Atom)





